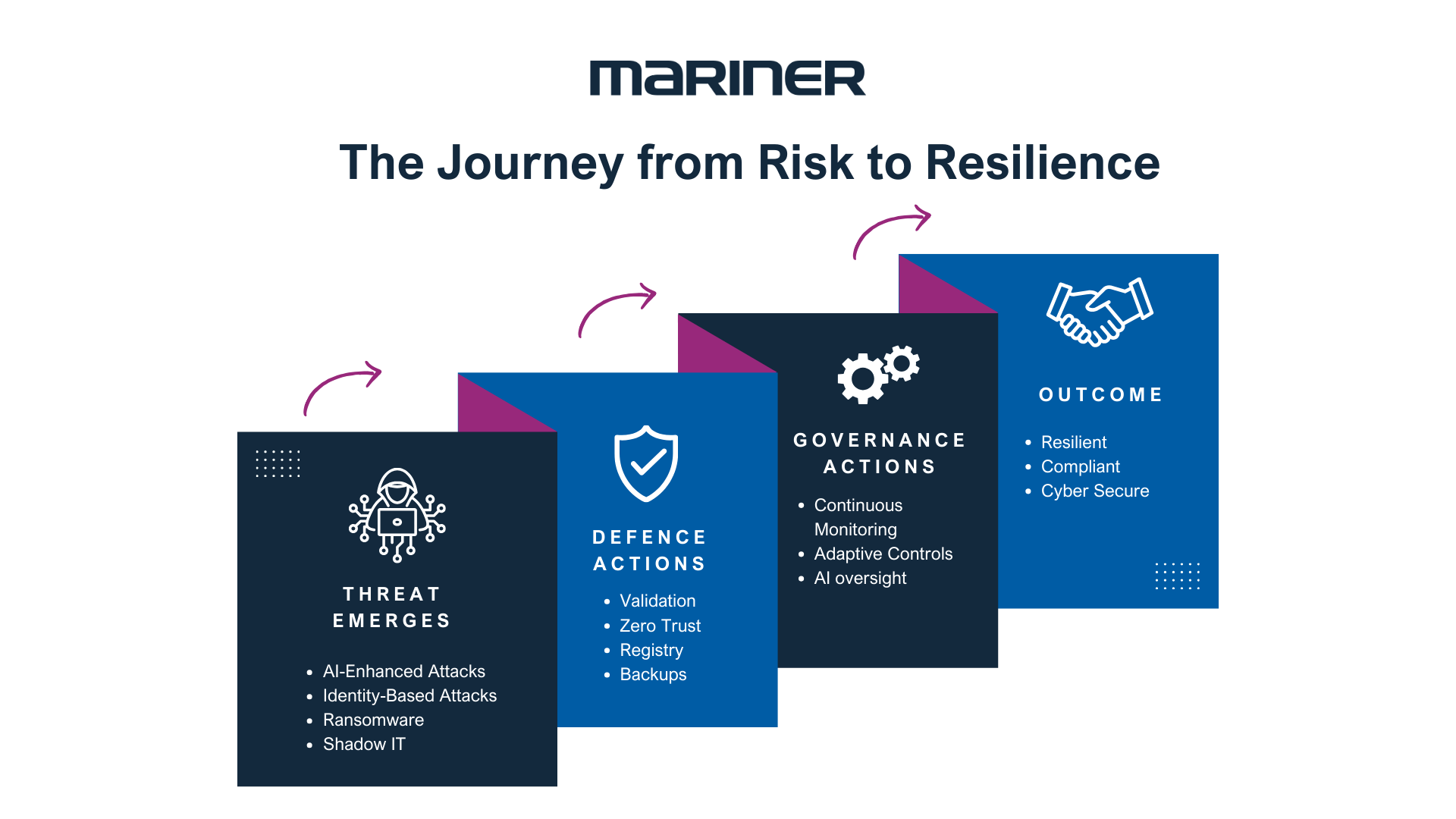
The Evolving Cyber Threat Landscape
Cyber risks are no longer distant or abstract. They are here today, evolving rapidly, and demanding immediate action from organizations of every size.
Artificial intelligence has changed the game for both defenders and attackers. Threat actors now have access to AI-powered tools that make their attacks faster, smarter, and harder to detect. To keep pace, businesses must combine AI-driven detection systems with human judgment. A machine can surface anomalies, but people are still required to validate high-stakes decisions. Simple practices such as verifying unusual requests through a phone call, enforcing email domain authentication, and double-checking out-of-band communications help keep organizations one step ahead.
At the same time, the perimeter of security has shifted. Firewalls and traditional boundary defenses are no longer enough. Identities have become the new perimeter. Zero Trust principles enforced multi-factor authentication, and least-privilege access are now fundamental building blocks of any security strategy.
Addressing Emerging Risks
Another challenge that organizations face is the rise of Shadow IT and Shadow AI. Employees often turn to unauthorized tools and applications to speed up their work. While this may feel efficient in the short term, it introduces serious risks. Data can be exposed, compliance gaps can emerge, and IT teams may be left in the dark about critical vulnerabilities. A practical way to manage this risk is to create and maintain a centralized registry of approved technology and AI tools. Combined with ongoing employee education and data loss prevention controls, this approach helps strike a balance between innovation and protection.
 Ransomware has also taken on a new and more dangerous form. Many attacks now operate as “extortion-as-a-service,” meaning that even smaller groups can rent sophisticated ransomware tools. This shift makes it easier than ever for attackers to launch devastating campaigns. The best defenses remain tried and tested: regularly exercising incident response plans, ensuring backups exist off-network, and confirming that those backups are both complete and functional.
Ransomware has also taken on a new and more dangerous form. Many attacks now operate as “extortion-as-a-service,” meaning that even smaller groups can rent sophisticated ransomware tools. This shift makes it easier than ever for attackers to launch devastating campaigns. The best defenses remain tried and tested: regularly exercising incident response plans, ensuring backups exist off-network, and confirming that those backups are both complete and functional.
Backups are only as strong as the last time you tested them.
Finally, we cannot overlook the human element. Technology is powerful, but people remain the last line of defense. Scenario-based training sessions, phishing simulations, and ongoing awareness campaigns give employees the confidence and instincts they need to recognize and resist sophisticated attacks.
Governance: From Periodic to Continuous
Strong cybersecurity requires more than strong defenses. It also requires effective governance. Historically, governance checks and audits were conducted on a periodic basis. Today, that is no longer sufficient. Threats evolve daily and systems change constantly. Continuous monitoring of controls and the use of real-time dashboards are now necessary to detect drift, enforce guardrails, and provide early warnings when something is not right.
Another important point is that internal controls must be adaptive. A single, one-size-fits-all model is not effective in a diverse business environment. Controls should be aligned with business criticality, threat exposure, and the frequency of change within each process. When organizations tailor their governance to their unique risk profiles, the controls are much more likely to deliver the intended protection.
 Auditability is also essential. Without proper evidence collection, organizations accumulate what is often called “compliance debt.” Policy attestations, access logs, and documented change approvals may sound administrative, but they form the foundation of credible compliance. Regulators, customers, and partners expect transparency, and without it, trust quickly erodes.
Auditability is also essential. Without proper evidence collection, organizations accumulate what is often called “compliance debt.” Policy attestations, access logs, and documented change approvals may sound administrative, but they form the foundation of credible compliance. Regulators, customers, and partners expect transparency, and without it, trust quickly erodes.
The Role of AI in Governance
Just as AI has created new risks, it also provides new opportunities for defense and oversight. Organizations should begin integrating AI-specific controls into their existing risk frameworks. These may include explainability checks, detailed logging of inputs and outputs, and rules governing how AI-generated recommendations are used in critical processes. Treating AI as another system subject to governance rather than a mysterious black box will make businesses stronger and more resilient.
Building a Culture of Resilience
Technology and controls are only part of the story. Culture is the control behind the controls. Employees at every level of the organization must understand that cybersecurity is not just an IT responsibility. It is a collective responsibility that touches every role and every process.
Creating this culture begins with ownership. Teams should be encouraged to raise concerns, question exceptions, and flag risks without fear of blame. Leadership can support this by embedding governance into daily business processes and by aligning performance metrics with adherence to security practices. When employees see that their vigilance is both valued and rewarded, they become active participants in resilience.
Culture is the control behind the controls.
A culture of resilience transforms security from a reactive function into a competitive advantage. Organizations that protect their data, operations, and reputation not only avoid damage but also strengthen their relationships with customers and partners. In an environment where cyber threats are accelerating, that advantage can make all the difference.
Every organization’s risk profile is unique.
Connect our team today to learn how we can help you build a cyber resilience strategy that fits your business.
Prepared By:
Chris Frame, Director, Business Information Systems
Rahim Pirani, Senior Security Advisor
Further Reading
Curious about other ways organizations can strengthen their security practices? Take a look at Pixelation Pitfalls: Safeguarding Sensitive Information the Right Way
