In today’s digital landscape, safeguarding sensitive information is paramount. Organizations often share documents containing screenshots that may include confidential data. A common method to obscure this data is pixelation, which blurs the sensitive content while maintaining contextual clarity. However, this technique is not foolproof and can lead to information leakage.
![]()
Pixelation reduces the resolution of the sensitive information, but it doesn’t eliminate the underlying data. Attackers who know the original content’s font and size can exploit this weakness to reconstruct the obscured information. Open-source tools like Depix facilitate this process by analyzing pixelated images and matching them against known character patterns to reveal the concealed text.
![]()
For example, using Depix, an attacker can analyze a pixelated password and potentially recover the original text. While the reconstruction may not be perfect, it often provides enough detail to compromise the sensitive information. In one instance, a pixelated password was successfully deciphered to reveal the phrase “Hello from the other side.”
To mitigate this risk, it’s advisable to use more secure redaction methods. One effective approach is to overlay sensitive areas with solid black boxes, ensuring the underlying information is completely obscured.
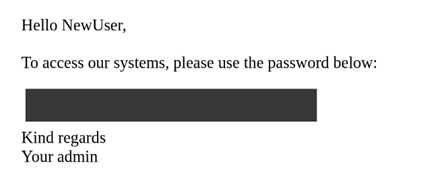
It’s crucial to apply these redactions directly to the image and save the final version in a format that doesn’t support layers, such as PNG or JPEG. This prevents potential recovery of the redacted information through simple editing techniques.
While pixelation may seem convenient for redacting sensitive information in screenshots, it poses significant security risks. Employing more robust redaction techniques, such as solid black overlays, is essential to ensure that confidential data remains protected. By adopting these best practices, organizations can enhance their cybersecurity posture and safeguard sensitive information from potential threats.
Ready to strengthen your cybersecurity defences? Contact Mariner today for expert guidance on securing your sensitive information and protecting your organization from potential threats. Connect with our team of cybersecurity specialists now!
