Cybersecurity Awareness Month is here and in celebration, the Mariner Vulnerability Assessment and Penetration Testing team are showcasing some of their favorite hacking techniques. Each week in October, they will explain a vulnerability, demonstrate how they might exploit it, describe its potential impact, and maybe even share some tips on how you can protect yourself.
Mariner penetration testing services span a wide range of domains – web and mobile applications, internal and external infrastructures, phishing simulations, wireless security assessments, and more. Testing is performed by combining real-world techniques with tried-and-true standards to provide a realistic picture of your organization’s security posture. Vulnerabilities are identified, analyzed, and broken down with prioritized remedial recommendations to help your IT teams strengthen defences where you need it most.
Check out the first two posts in our series: Stealing User Credentials with Open Redirects and SQL Code Injection
Wireless networks are one of the most common avenues threat actors will take to gain access to your internal systems. Once breached, wireless networks often offer attackers a valuable foothold to pivot onto other networks in your organization, jumping from host to host until your entire environment is compromised. This week’s article is going to examine how the 4-way handshake for Wireless Lan (WLAN) communication works, how an attacker might compromise that process, and how to improve your wireless security posture. Businesses and private individuals alike need to be aware of how easily a threat actor can compromise their wireless networks and how they can protect themselves. To better understand how to attack and defend a wireless network we must understand how wireless clients establish a secure communication channel with an access point.
Wireless Authentication
So how does a wireless client like a cellphone achieve secure communication with a wireless access point (AP)? How does the client and AP share the secrets necessary to do this? Enter the 4-way handshake. Explaining the 4-way handshake in technical detail is outside the scope of this article but fundamentally, the process uses device-unique identifiers, randomly generated numbers, and the wireless password to generate what is called a Pairwise Transient Key (PTK). This PTK is then used to encrypt the traffic sent over the airwaves between the client and wireless AP.
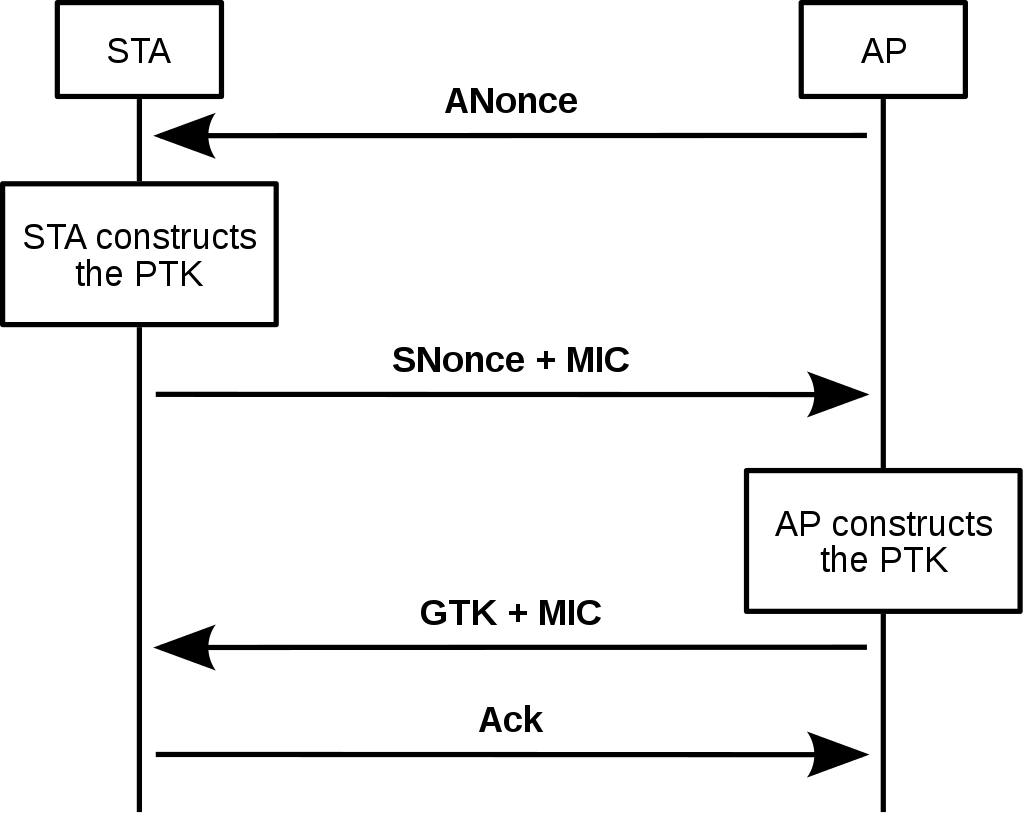
Now that the 4-way handshake is complete, encrypted data can be sent securely. However, threat actors can eavesdrop on this process to deconstruct the PTK, and potentially steal the encrypted wireless password.
To further understand the history of wireless computer communications and the technical standards that regulate them, refer to IEEE 802.11.
Attacking a Wireless Network
A threat actor may set out to compromise sensitive data, perform illegal activity from a victim network, or simply access free internet. Whatever their end goal is, a wireless network is a prime target for achieving it. This is because wireless networks are often accessible well beyond a business or residential boundary and may not be closely monitored for unwanted clients. There are many ways to attack a wireless network, this article focuses on compromising a typical Wi-Fi network by capturing the 4-way handshake.
As the threat actor, they might drive around an area scanning for wireless networks they want to attack (a tactic called Wardriving) or they may position themselves outside a target business or residence. They can use any number of tools to detect wireless networks being broadcast nearby and collect data on them, including signal strength, security type, SSID, etc. Hidden networks are not safe from these tools.
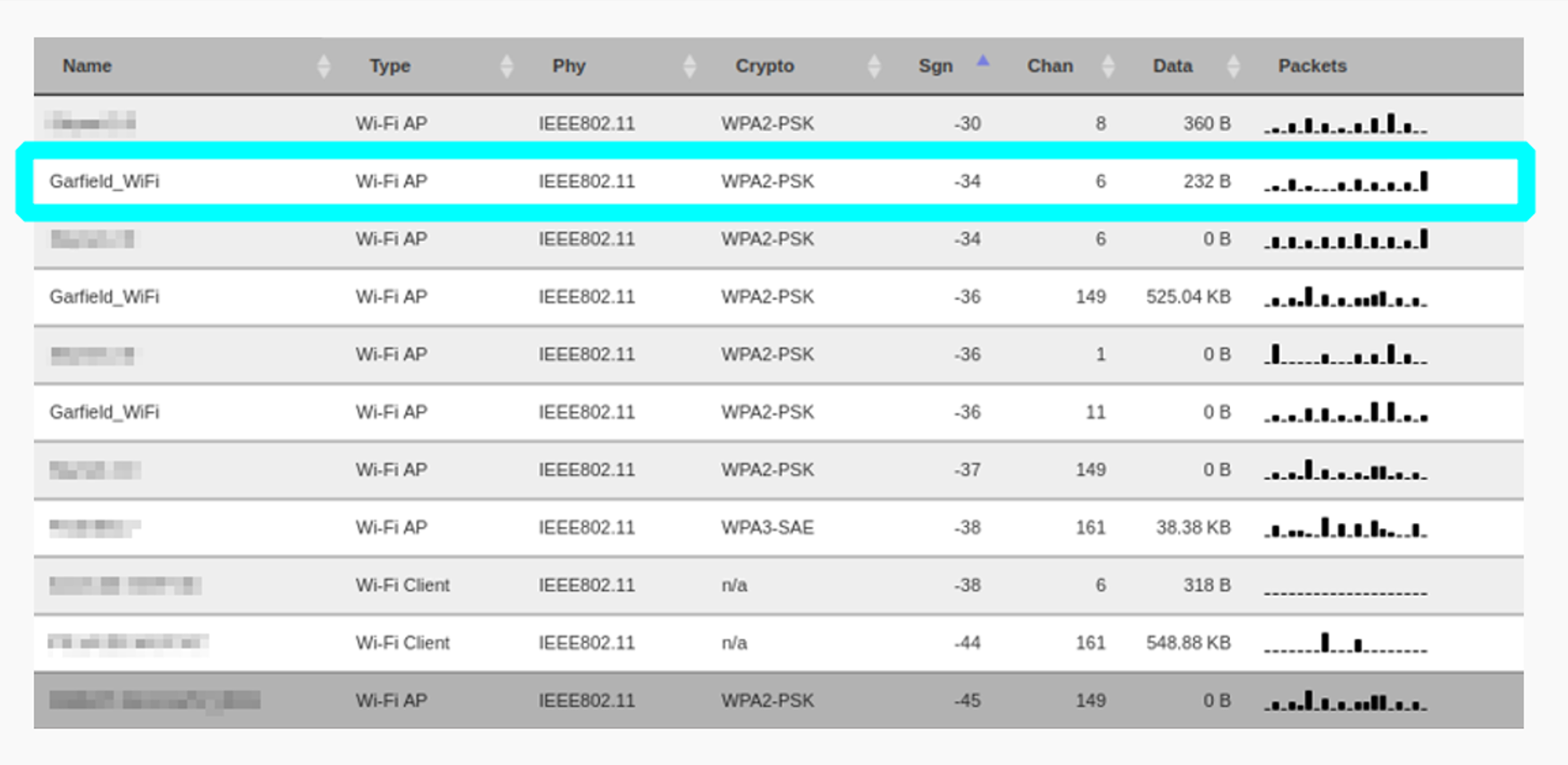
Scanning for and selecting a target network
Once they’ve selected a target, they can park their van inconspicuously and get to work. This attack works against WPA2, the protocol used in most of the networks on the list above, but this method is also effective against the weaker and (hopefully) less often seen WPA and WEP protocols as well. Now that a target has been selected, they will monitor the network for a connecting client, or they can attempt to kick a client off the network and trigger reconnection.
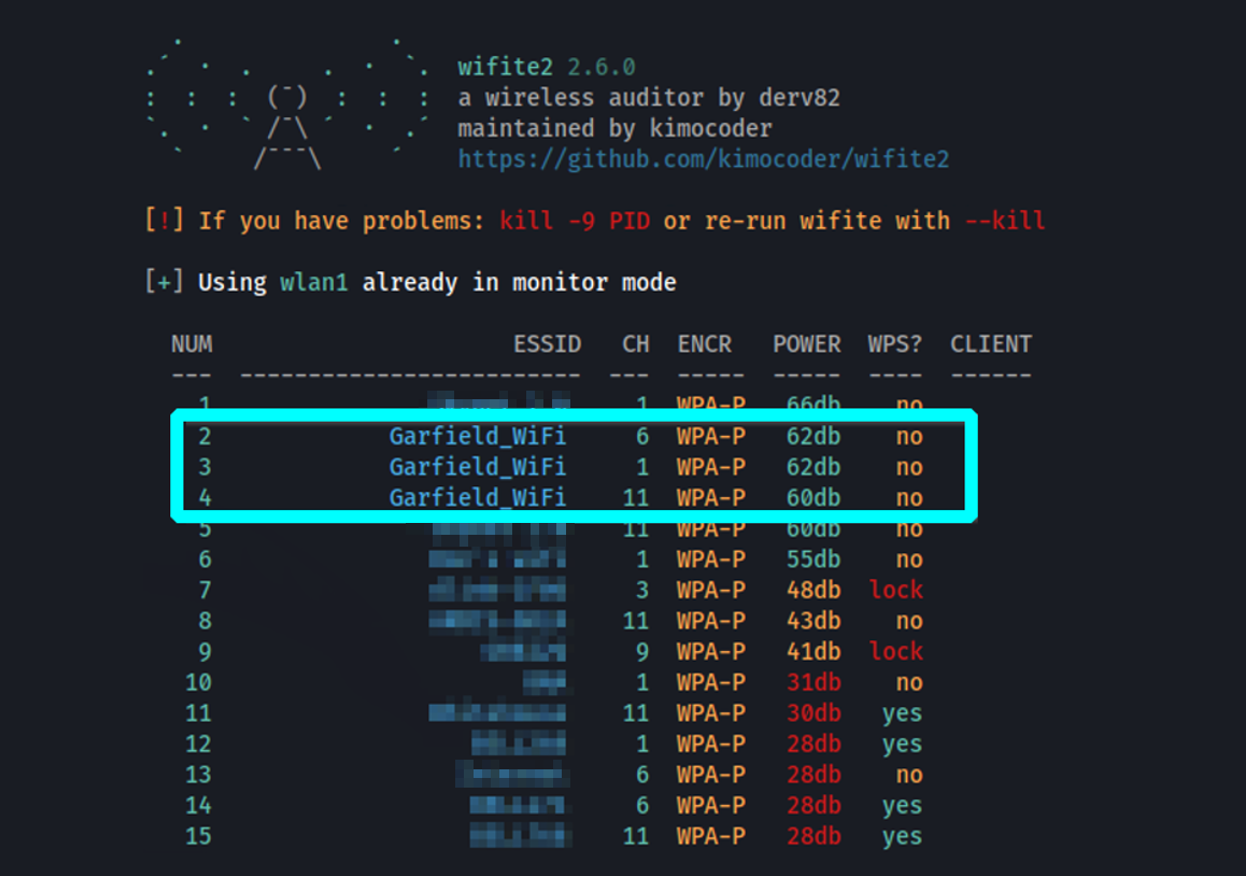
Identifying APs serving the target network
The threat actor wants to capture the 4-way handshake which is only performed when the client is making that initial connection to the network. A de-authentication attack, which kicks the victim off the wireless network, is useful when we are attacking a network that does not have a high volume of new clients connecting to it. This is because kicking the user off the network would induce them to reinitiate the authentication process. Wifite is an excellent tool that will automate the de-authentication process and attempt to capture the 4-way handshake for us.
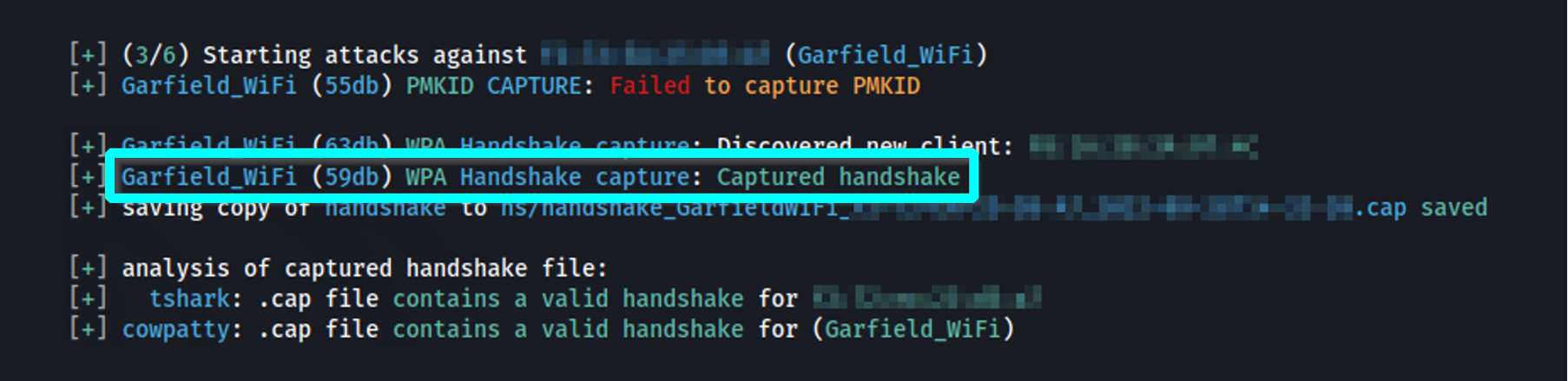
Using Wifite to successfully capture a 4-way handshake during the wireless network authentication process
Once the handshake has been successfully captured, the attacker can extract the encrypted wireless password and attempt to crack it. Depending on the complexity of the password and the power of our password-cracking computer, this could take hours, days, or more to “brute force”, or guess, every possible combination of numbers, letters, or symbols. Diligent threat actors will consider likely words or phrases that might be used in the password to reduce the time it takes to crack it. In this case, the wireless network is named All Posts“Garfield_WiFi”. A keen threat actor would create a wordlist of possible words associated with this familiar orange cat; lasagna, orange, lazy, etc. Then, this wordlist would be sent through a formula to create permutations, generating common variations of the words in the list. For example, the formula might replace A’s with 4’s, S’s with $’s, append numbers, symbols, so on and so forth.
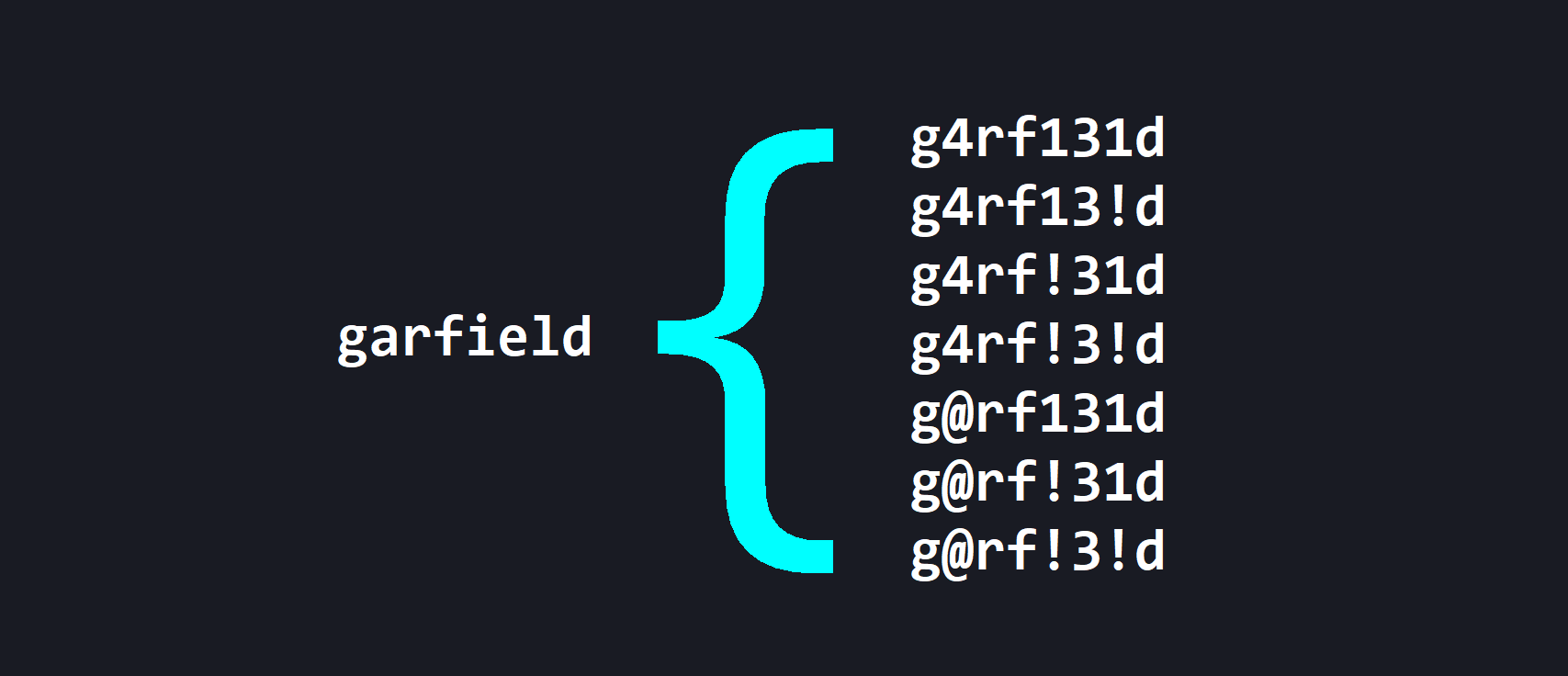
An example of how permutations of a word might be generated
With luck, the attacker will have success with their custom wordlist. The captured handshake and custom wordlist are fed into Hashcat, a tool used to crack values encrypted with various encryption algorithms.
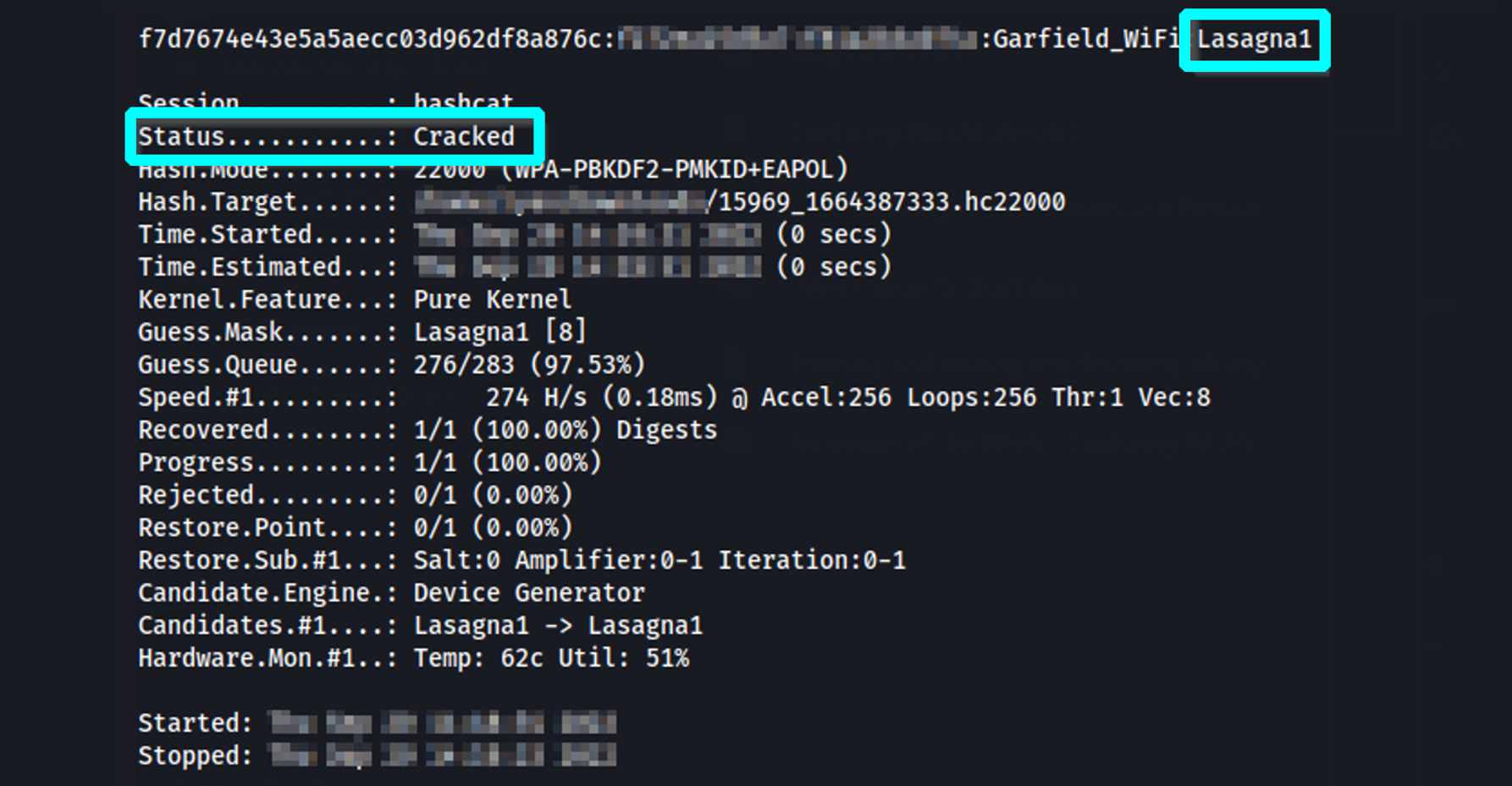
Successfully cracking the wireless password Lasagna1 with Hashcat
Once a threat actor has determined the wireless password, they can connect to the wireless network to perform any number of nefarious actions including:
- Enumerating clients as possible lateral targets
- Pivot onto other internal networks
- Accessing or manipulating vulnerable files or systems
- Attempt to compromise network-attached devices
- Use the network as a base for illegal internet activity
Harden a Wireless Network
The 4-way handshake capture technique described in this article is just one example of how a wireless network can be compromised. Below are some tips on how to harden your wireless network against threat actors.
- Use the Latest Security Standards – As a minimum, WPA2 or WPA3 should be used as they are harder to crack than legacy protocols. Never use deprecated standards such as WEP and WPA.
- WPA2-Enterprise Over WPA2-Personal – WPA2-E’s 4-way handshake uses a unique master key for each connection rendering more attacks unrealistic. Clients must also supply unique credentials as opposed to a single pre-shared key to connect.
- Password Complexity – Wireless passwords should be at least 12 characters long and not easily guessable. Never leave a wireless network unprotected without a password.
- Disable Wi-Fi Protected Setup (WPS) – WPS is trivial to brute force, and threat actors can typically crack it in a matter of seconds.
- Reduce Signal Output – Decrease the wireless signal range so that it does not extend outside the premises of your site.
- Segregate Networks – If feasible, keep wireless networks separate from your corporate network. Never allow access to internal resources from guest wireless networks.
Do you make use of wireless technologies in your organization’s facilities? Is your network security robust enough to withstand a targeted attack? Mariner offers Wireless Security Assessments to help businesses achieve the strongest security posture possible, mitigating the risks of sending traffic over the airwaves. Connect with us today and speak with one of our vulnerability assessment and penetration testing experts.
—
Ryan VanSickle, Cybersecurity Analyst
Let’s Connect
