Cybersecurity Awareness Month is here and in celebration, the Mariner Vulnerability Assessment and Penetration Testing team are showcasing some of their favorite hacking techniques. Each week in October, they will explain a vulnerability, demonstrate how they might exploit it, describe its potential impact, and maybe even share some tips on how you can protect yourself.
Mariner penetration testing services span a wide range of domains – web and mobile applications, internal and external infrastructures, phishing simulations, wireless security assessments, and more. Testing is performed by combining real-world techniques with tried-and-true standards to provide a realistic picture of your organization’s security posture. Vulnerabilities are identified, analyzed, and broken down with prioritized remedial recommendations to help your IT teams strengthen defences where you need it most.
Check out the first three posts in our series: Stealing User Credentials with Open Redirects, SQL Code Injection and Cracking Wireless Networks.
It seems that each time a cybersecurity hole is fixed, workarounds are eventually found. It is kind of like the three little pigs in a way; cybercriminals will continue huffing and puffing until the house is blown down. Build a higher wall and threats bring taller ladders. Dig a deeper trench and threats bring bigger shovels. Add a second authentication check, and threats bring more sophisticated tricks to bypass it. If there is something of value to be taken, the arms race will continually perpetuate.
The Human Factor
Phishing tactics take advantage of human nature, and this is a vulnerability that is nearly impossible to prevent completely. It is also a very effective method for threat actors to gain initial access to corporate systems by stealing valid credentials from unsuspecting victims. Once inside an employee’s email or file system, the information that can be obtained can most likely allow for outright privilege escalation or can be used to target higher privileged users. The next step would be to set up persistent access and hide undetected while gathering sensitive data or avenues of access to be sold on illicit markets. Multi-Factor Authentication (MFA) was designed to stop these types of attacks by requiring more than just valid credentials to grant access to resources, typically through a unique code sent via SMS or an “Authenticator App”. Of course, it was only a matter of time before threat actors and security researchers were able to reverse engineer and find workarounds to bypass this MFA. The accessibility to technology in our pockets 24 hours a day 365 days a year can also cause complacency. The bad guys are willing to take advantage of this and catch their targets when they least expect it.
How This Attack Works
The method for bypassing MFA is not that complex, and there are free tools out there that with very basic knowledge, can be used to perform an attack in a matter of minutes. The attack works by hosting a fake login page on the internet for the credentials the attacker intends to steal. The threat actor will attempt to convince someone to log in to their fake login page, usually by sending a malicious link in a phishing attack. Should the user fall victim, the threat actor would now have access to the victim’s credentials for the account the attacker was trying to steal. Under normal circumstances, this would be enough to compromise the user’s account. But what if the user had MFA enabled?
In this example, the attacker is attempting to compromise a victim’s email account. The attacker hosts an identical login page to the one the user would typically use to log in, and configure it so it appears completely legitimate to the untrained eye.
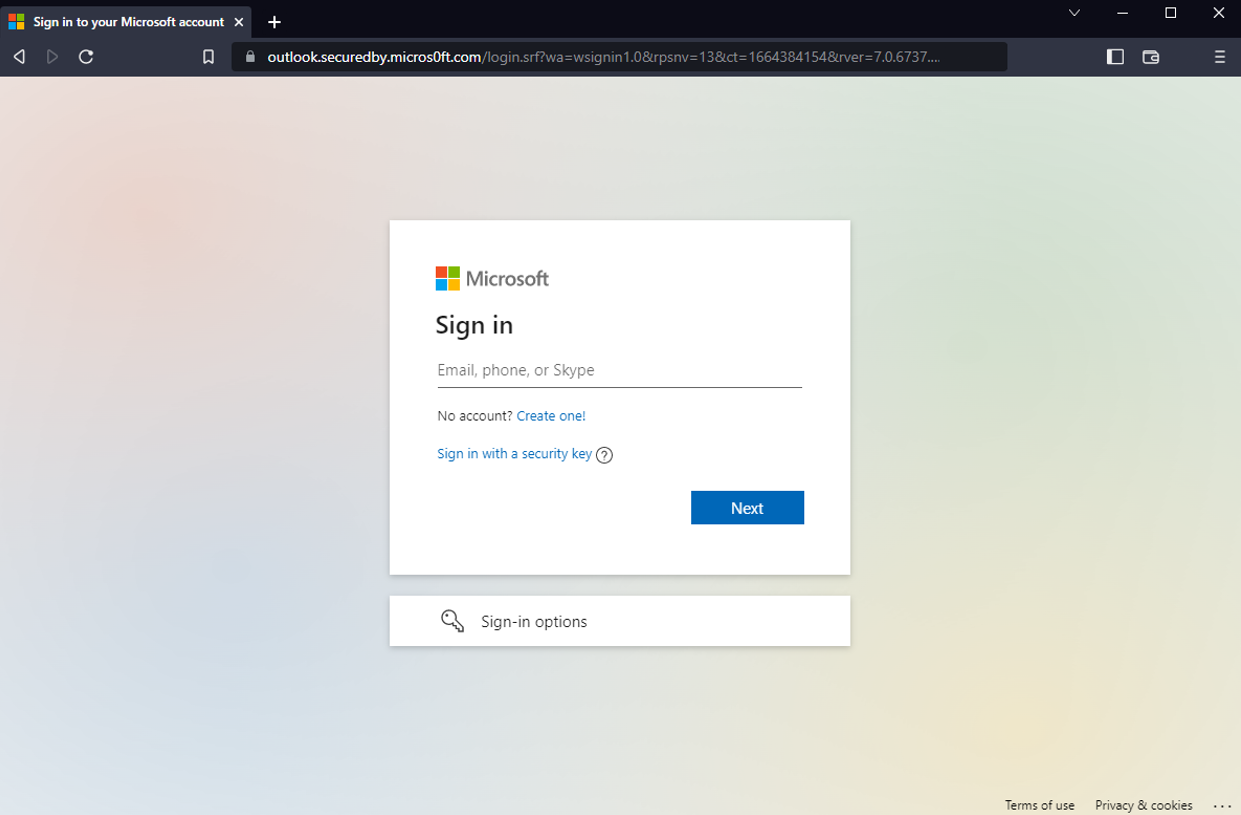
The fake login page hosted by the threat actor. Could you tell the difference between this and the real one?
Using publicly available tools, the attacker can configure the fake login page to act as a proxy, an intermediary system between the victim and the real login page the attacker is impersonating. Because the threat actor is in control of this proxy server, everything that is sent to and from the fake login page and the user’s browser is visible to the threat actor. This proxy can be configured with web certificates so the “lock” will still appear in the address bar of the user’s browser. Should the user enter their username and password to the fake login page, the attacker’s server would forward the credentials to the real page. If the user has MFA enabled, the proxy would receive the MFA request from the real login page and forward it to the victim.
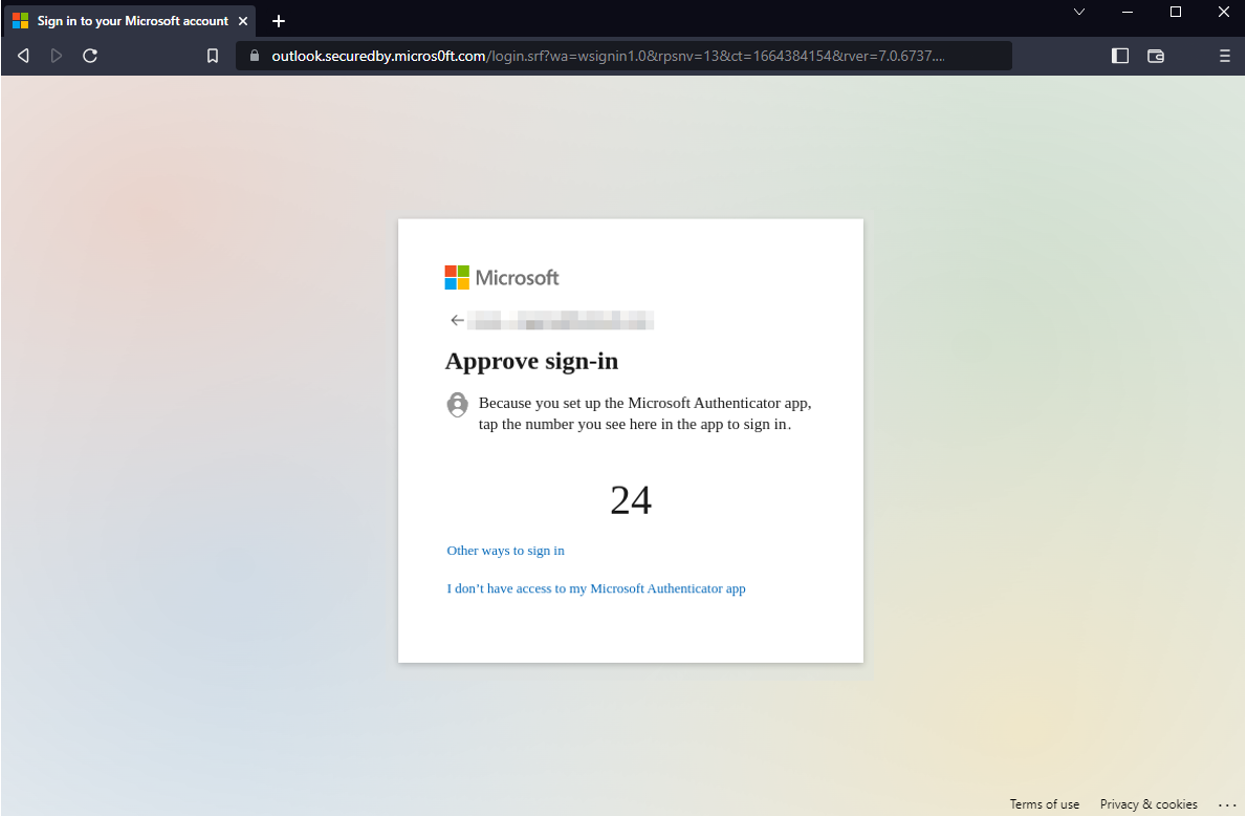
The fake login page relaying the MFA request from the real login page to the victim
The user would then perform the MFA action prompted in the sign-in process. The MFA response would then be proxied through the fake login page, to the real login page, forming a valid session with the email application.
Behind the scenes, the attacker captures all of the information sent through the fake login page. This includes the username, password, MFA response, and most importantly, the valid session token.
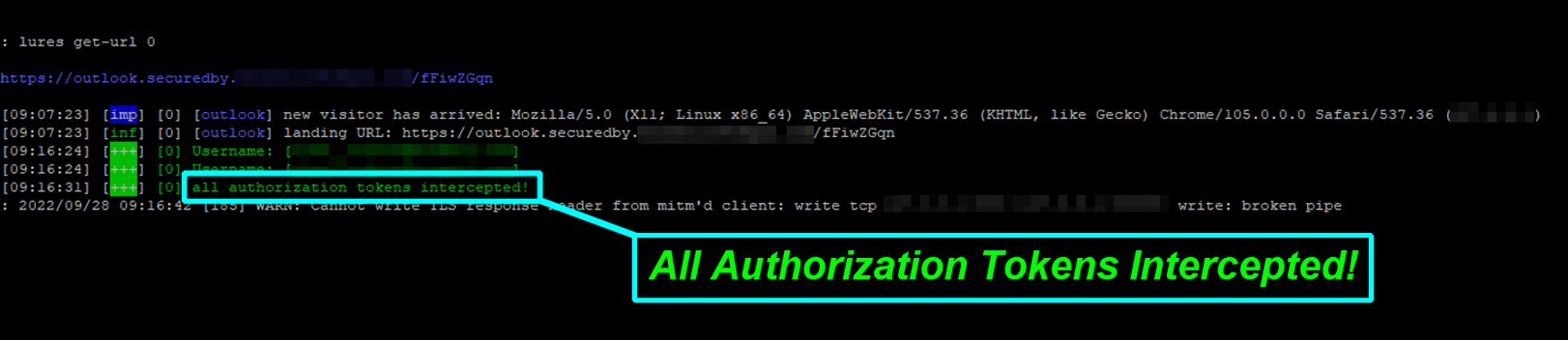
Behind the scenes of the attacker’s fake login page. The information captured here is used to compromise the victim’s account.
The threat actor is now free to use the captured session token to hijack the valid session. For as long as that session is valid, the threat actor can perform actions and queries as the victim. If a company was using Single Sign On with low security standards, it could be catastrophic should the wrong user give access to a threat actor that is prepared to propagate malware within an environment.
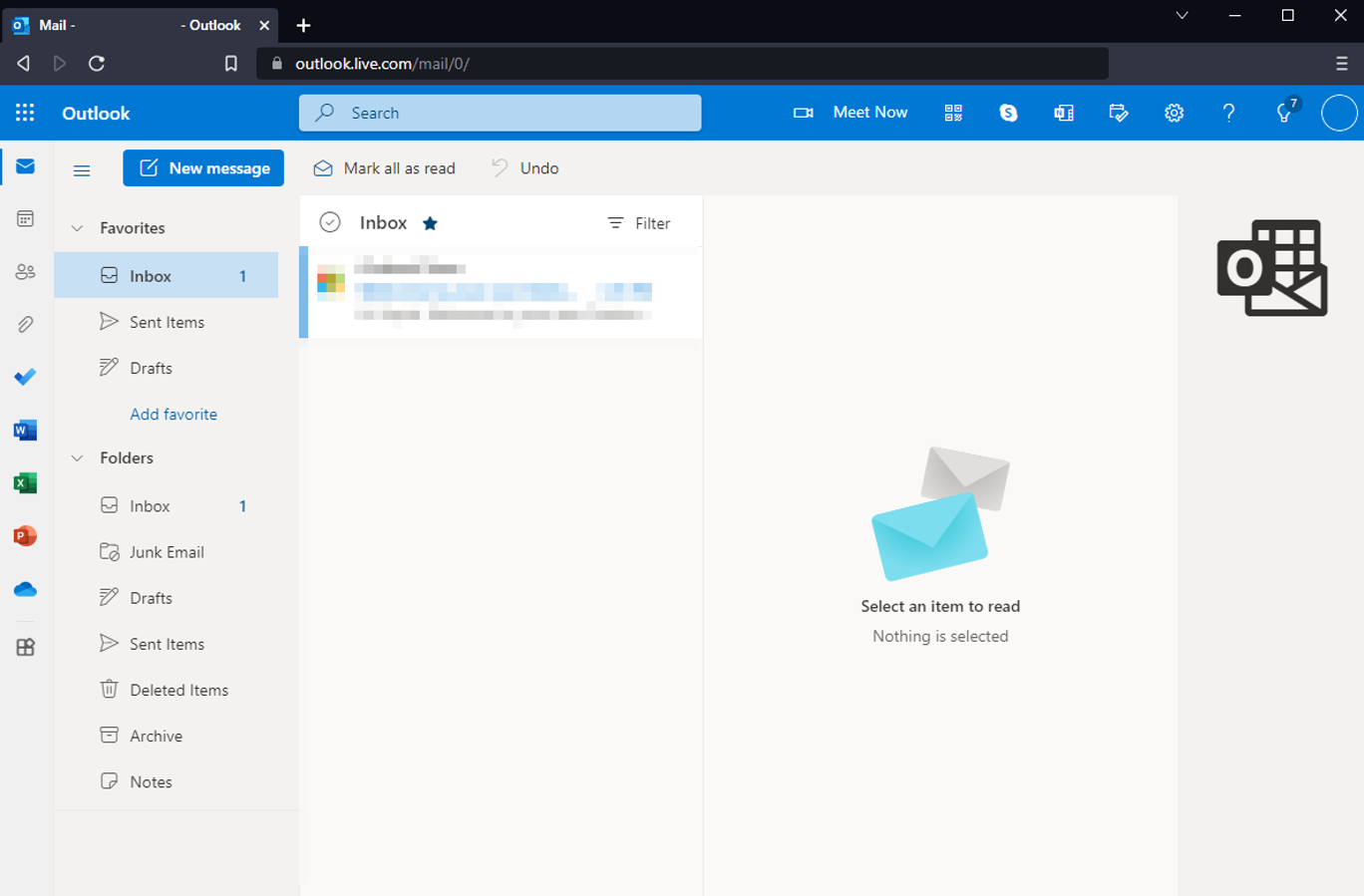
The attacker uses the captured session token to hijack the victim’s session, giving complete access to the victim’s email account — even with MFA!
Can it be Stopped?
Unfortunately, social engineering attacks can only be fully prevented by removing humans from the equation. Because that is not a practical solution, we can only hope to educate users so that they become more cyber-aware, and trained to identify security threats, most notably phishing attacks. Threat actors can use techniques to make phishing lures look quite convincing, and sometimes, complacency can even catch seasoned security professionals off guard. An additional important consideration is to implement security controls to minimize the impact of a successful breach. With regular user education and help from security experts who specialize in exposing and bolstering an organization’s posture, we can lower the severity when these sometimes inevitable events occur.
How Can Mariner Help
Mariner has a diverse security team that can assist your team in identifying gaps and hardening security architecture. One of our offerings includes a realistic phishing simulation that tests the human side of your organization’s security. Extensive Open-source intelligence OSINT gathering is performed and used to craft highly sophisticated, targeted phishing attacks, and the results paint a picture of just how keen your users are.
If you are interested in seeing how prepared your organization is to withstand a realistic phishing attack, connect with us today!
Ryan Rogers, Cybersecurity Consultant
Let’s Connect
